In recent years, more and more companies prefer to install VoIP-equipment, in order to save on telephone. However, the purchase of low-quality devices, their clumsy setup, without taking into account all the stages of protection against hacking is a direct path to the introduction of hackers into the system.
In addition, many believe that they will be able to install and configure the gateways on their own. But in most cases, users do not know how to correctly and consistently protect their system from hacking. Not understanding how the GSM gateway operates, they neglect measures to protect VoIP systems from hackers.
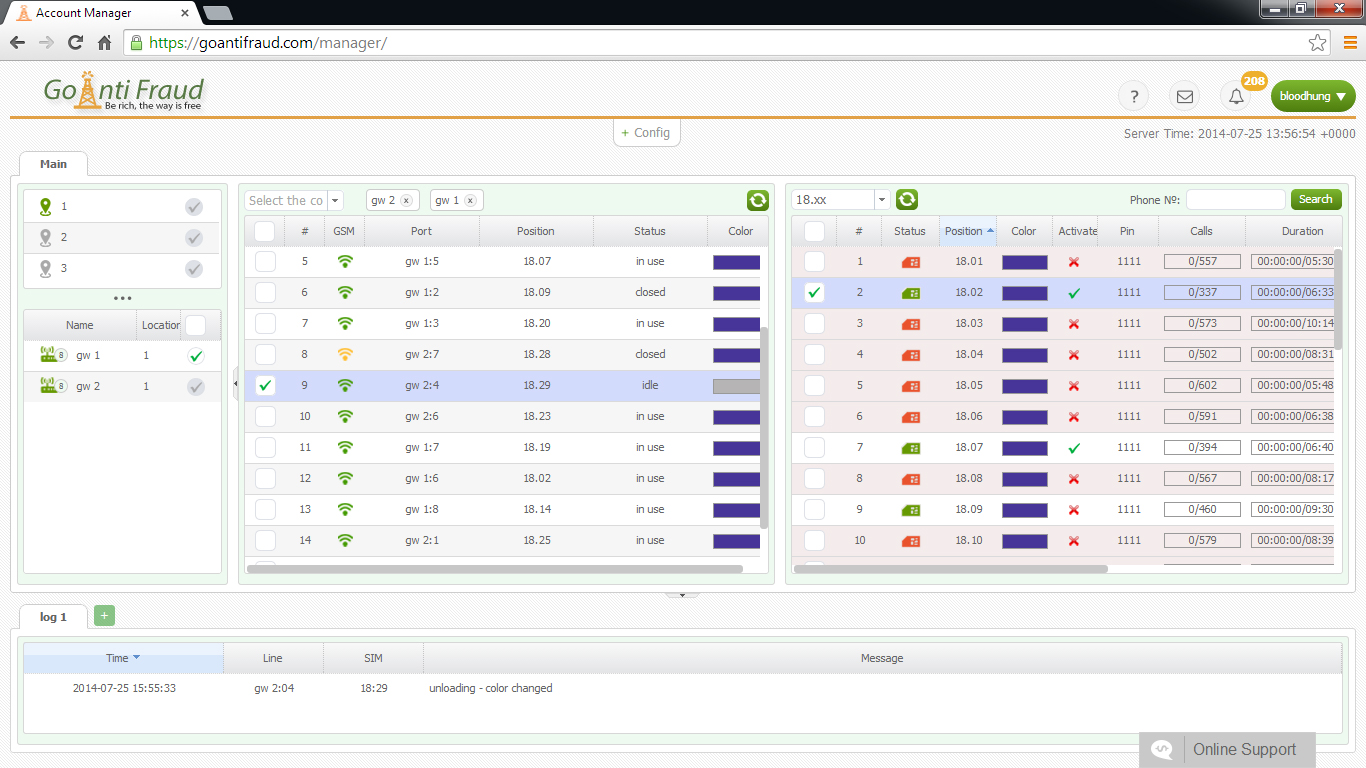
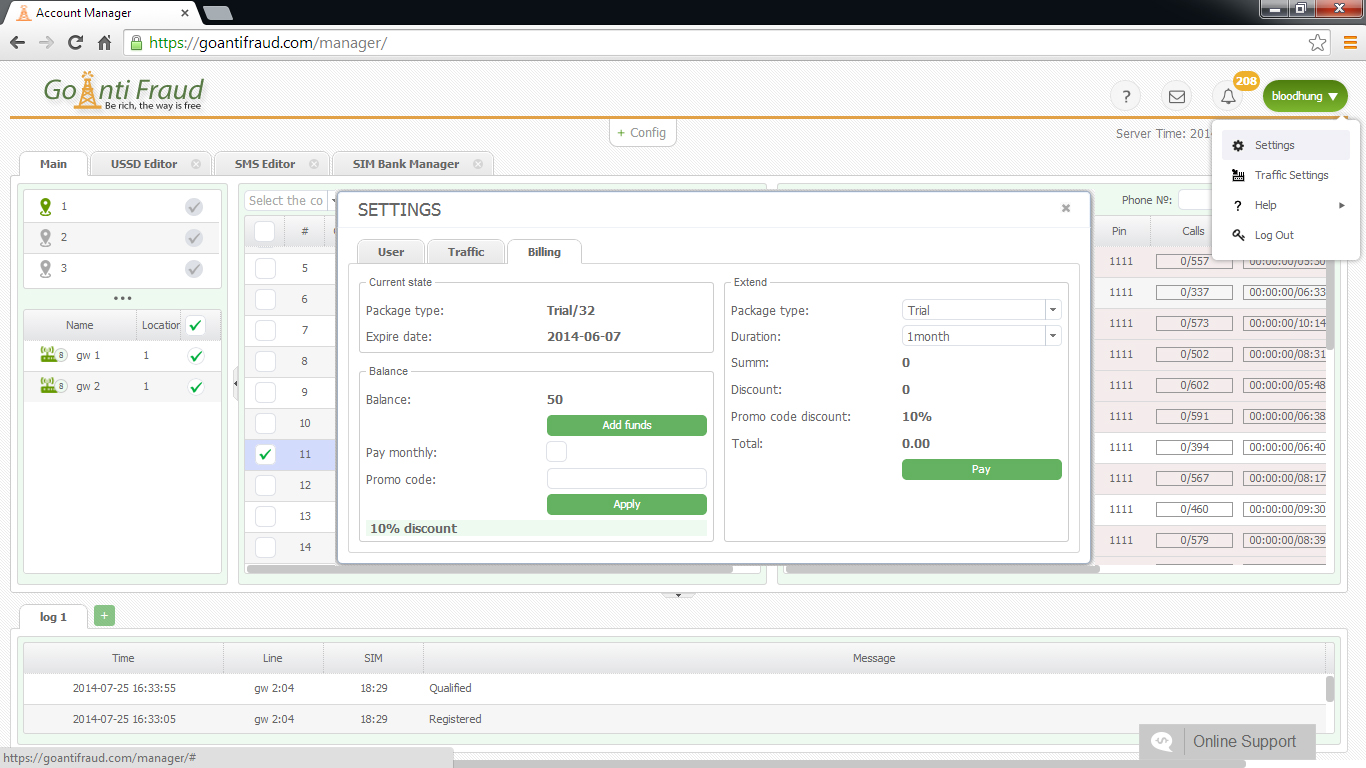
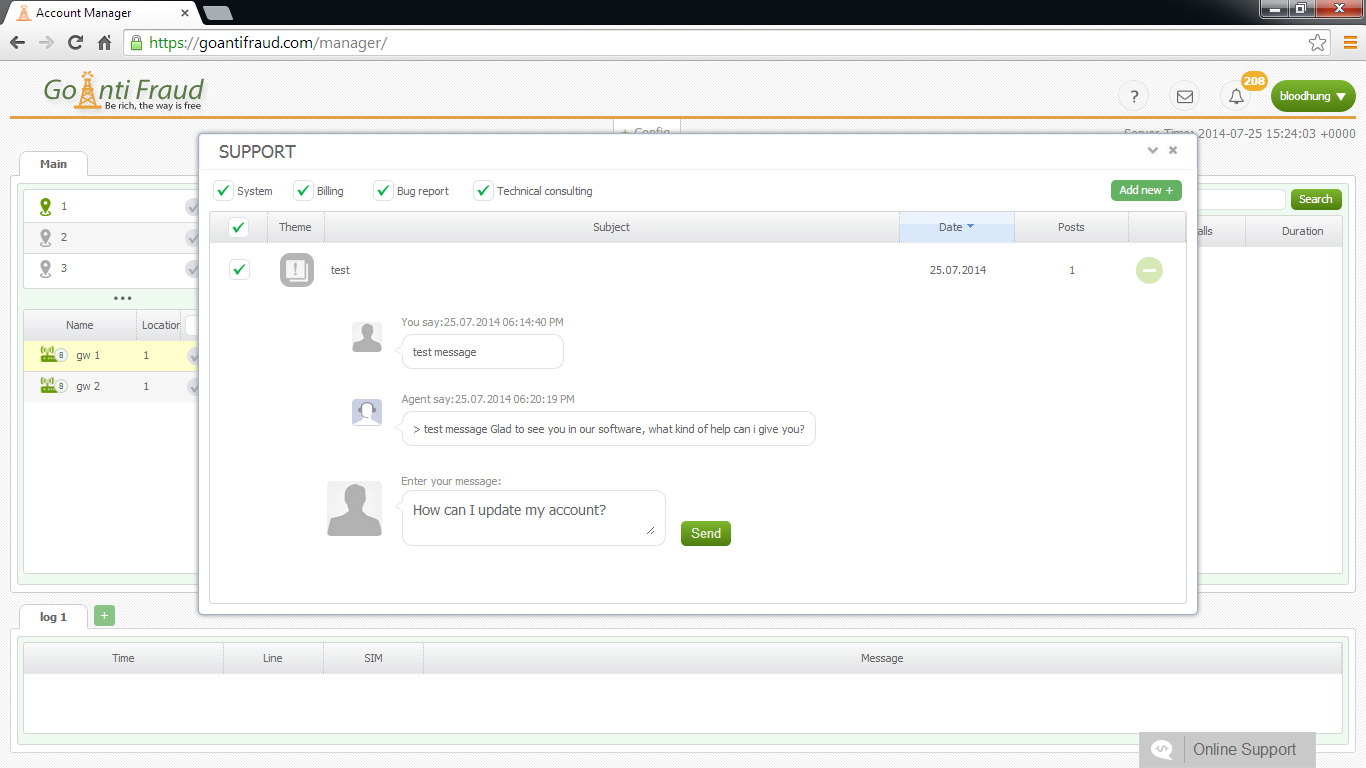
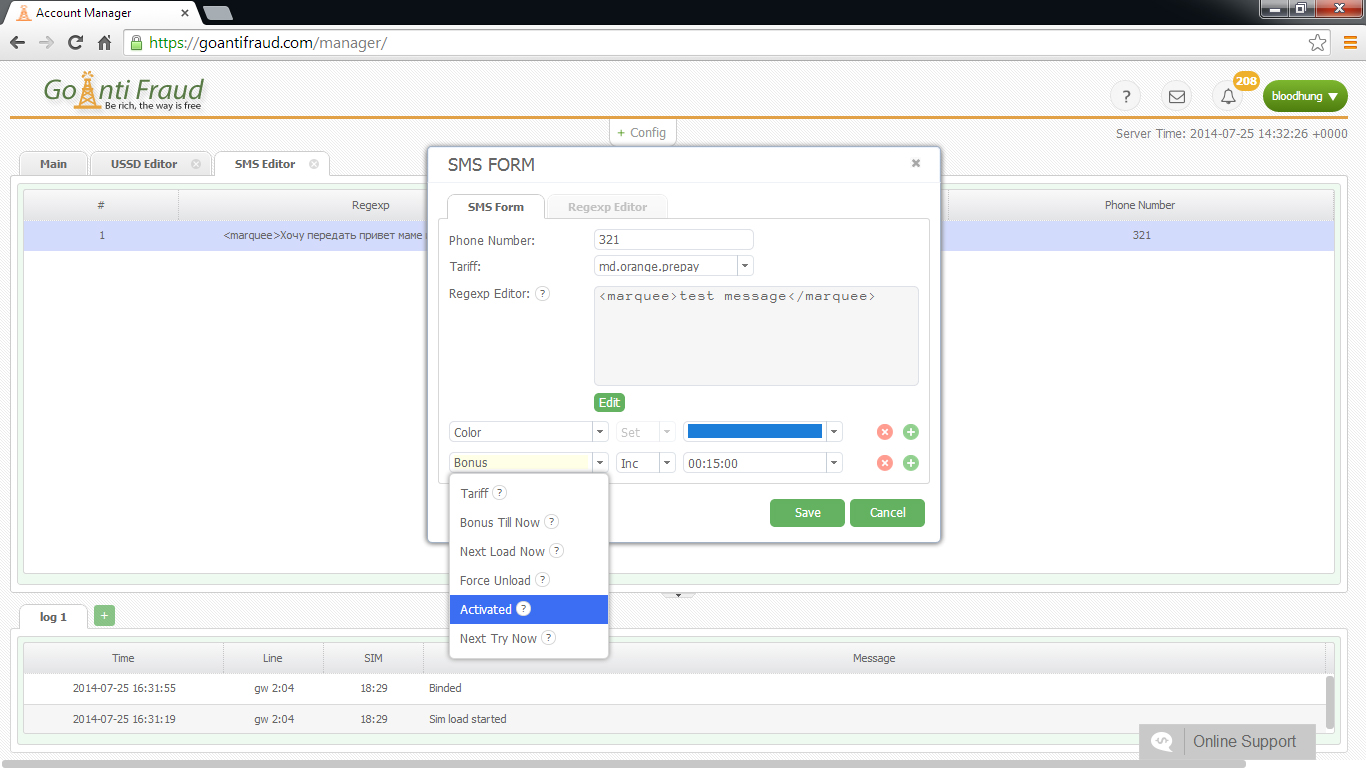
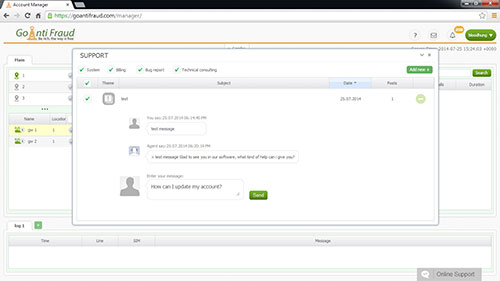
It is important to use a special log to collect data on security issues, which should always be followed. However, most beginners do not even know that it exists. In addition, when beginners install gateways and configure the PBX, they set simple passwords, or do not so at all. Many mistakes are also made when separate networks are set up for VLAN and traffic is adjusted on the router. It is understood that such technical illiteracy to create a VoIP system can only play into the hands of hackers.
GoAntiFraud offers you to start a profitable GSM termination business! If you are interested in VoIP technology, we will help you start your own business, yielding a stable income. By purchasing our comprehensive New Business package, you will start making money immediately! We will give you full technical support at all stages of business.
On forums, newcomers keep saying that the system does not read the main protocols, including SIP. Failure to account for the control of content results in information not being transmitted. It is the main reason for its incorrect work and vulnerability to hacker attacks as hackers can easily modify the underlying protocol in the system.
In addition, it is difficult for ordinary users to set up a reliable protection in traditional firewalls, not to mention the MITM encryption and MAC address. It is important to remember that Asterisk system is the most vulnerable to hacking. And if you do not use protocols SRTP/ZRTP, TLS/SSL and set complex passwords, data access remains open, regardless of the use of other functions.
Asterisk must be set up carefully because when hackers select keys, they can easily analyze the system answers and find out the available extensions to gain access to the server. From this point of view, users should bear in mind that the protection of the systems needs a comprehensive sound approach to block threats at all levels. It is better to immediately purchase a top-quality GSM VoIP-gateway and turn to experts.
Are you interested in VoIP technology? Are you looking for a reliable start-up in the telecommunications sector? You will be interested in the opportunity to start a GSM termination business. You can get the maximum profit making the minimal investment! We offer a turnkey GoAntiFraud solution for beginners, which includes opportunities for efficient VoIP termination, as well as a set of equipment by GoIP, EjoinTech & China Skyline at low cost.