Failing to connect the gateway, beginners faced hacker attacks, which is fraught with the loss of traffic. Unfortunately, the voice Gsm Sip Gateway can conduct calls via any IP-addresses, thereby providing traffic for fraudsters. For that reason, the issue of protection becomes relevant.
The network connection problem occurs when you install Asterisk VoIP. When connecting gateways, calls usually come from certain numbers, for example, from 8102526, and make lines in the equipment busy and difficult to get. Beginners complain that there are no downloads on calls in the asterisk login, with the device operating via an external IP. The connection is protected with passwords, which are not a barrier for traffic stealing.
To infiltrate the system, the only thing the attacker needs to know is the IP-address of the gateway. Then he sends the call setup message, for example - SIP INVITE, H323 SETUP. In the absence of a white IP-address, the hacker makes calls at the expense of the subscriber. The Internet provider provides access to NAT. Thus, the hacker is connected via the IP-address and outputs his data as those of the provider.
The attacker typically has access to many of the services that are provided to the client VoIP by the provider. Fraudsters realize the SIP-account in many of their schemes, employong the PRS, to make more calls to different directions.
A hacker can infiltrate via SIP as well. This protocol is designed to carry out a session and further data transfer. The problem is that he transmits information in the clear. There are credentials for the subscriber, indicating the username, domain, password, and other information that is easily intercepted by hackers for future use. Experts also call this attack MITM.
Are you interested in VoIP technology? Are you looking for a reliable start-up in the telecommunications sector? You will be interested in the opportunity to start a GSM termination business. You can get the maximum profit making the minimal investment! We offer a turnkey GoAntiFraud solution for beginners, which includes opportunities for efficient VoIP termination, as well as a set of equipment by GoIP, EjoinTech & China Skyline at low cost.
A DNS attack is carried out by an MITM or by sending cache when a hacker can impersonate a provider. An attacker usually directs client calls to a free number that do not even exist. Then he intercepts INVITE packages and answers to the request from 301 Moved Permanently, redirecting the call.
Choosing FromTag, Call ID, ToTag, the hacker interrupts the active session, sending complex packages containing SIP BYE-request and the request to the completion of the connection via scapy.
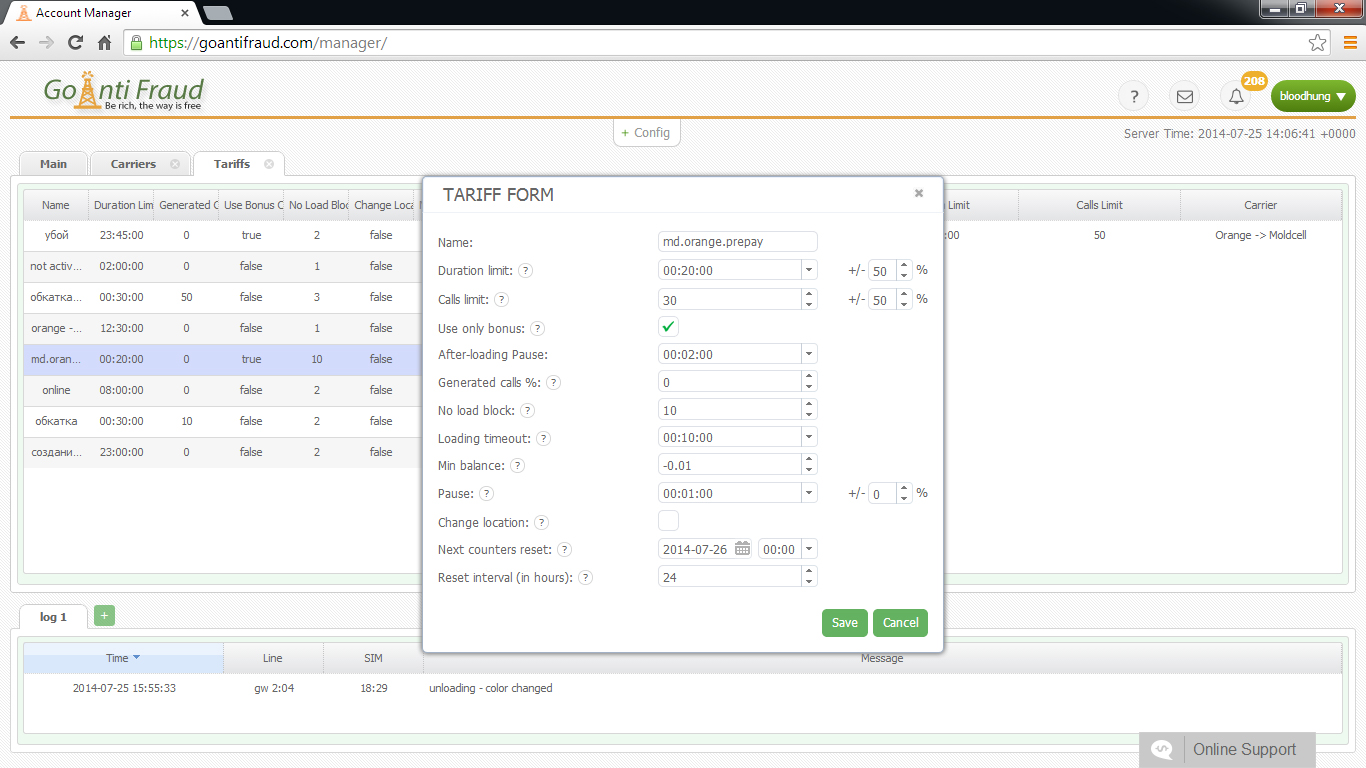
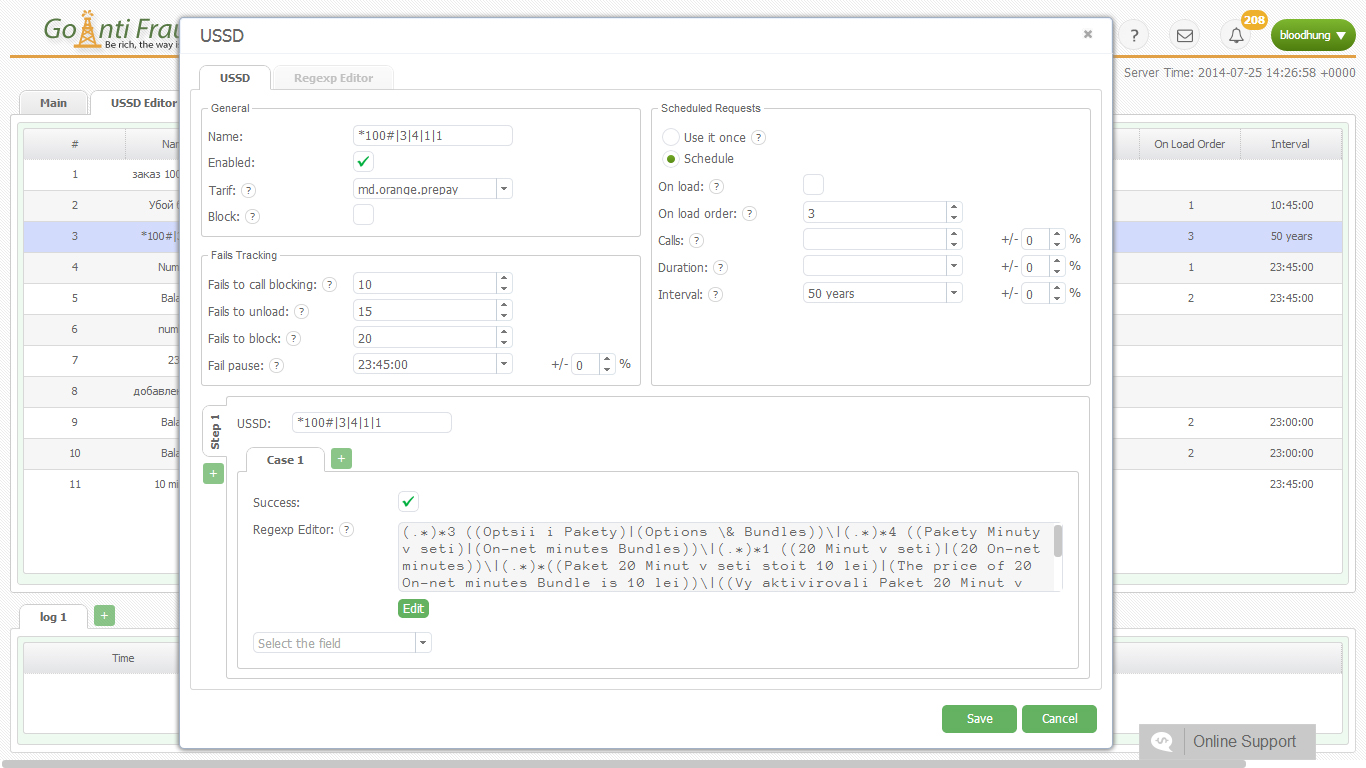
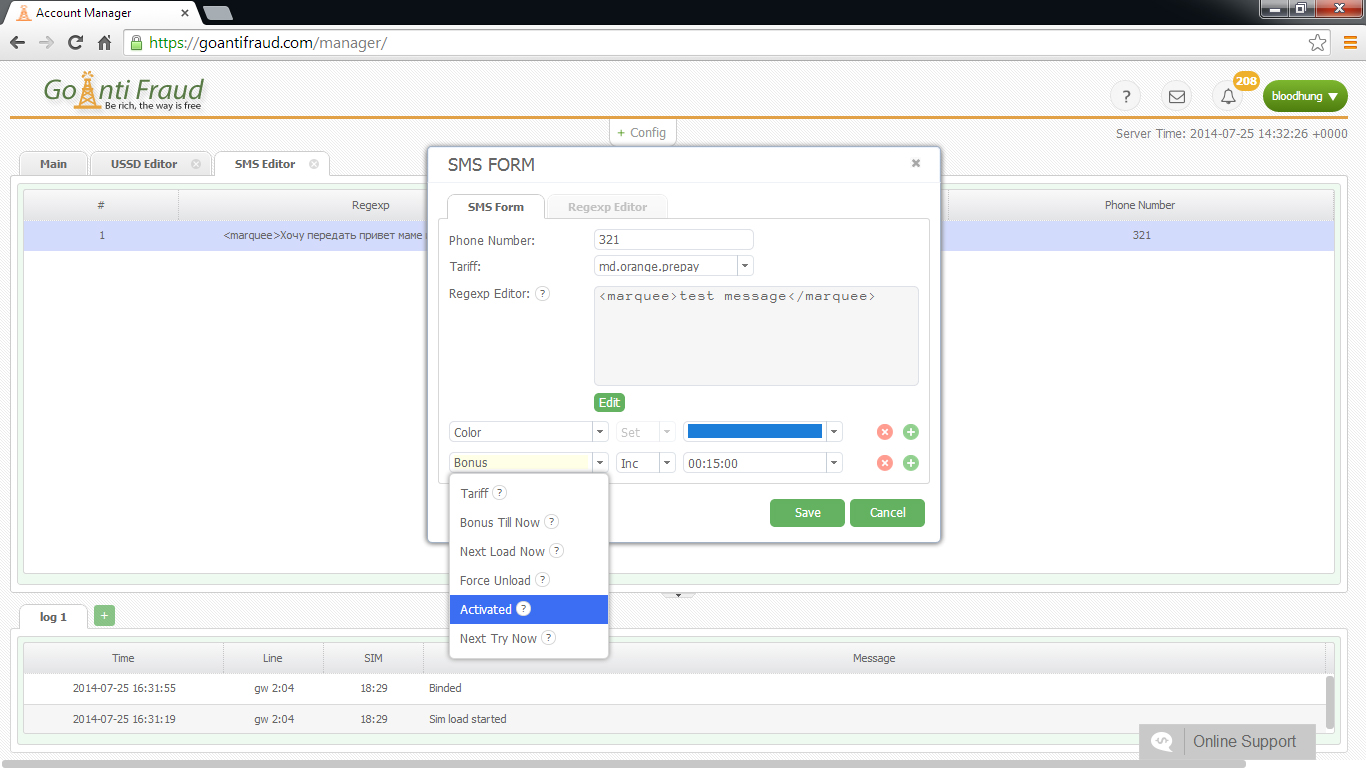
For this reason, experienced terminators advised not using the standard ports for signaling protocols (H.323 = 1720 or SIP = 5060). Also, to prevent hacker SIP attacks, it would be enough to enter trusted addresses andallow incoming calls for H323 trunks and SIP from the 10.1.250.101 address, specifying VoIP and the IP, including ipv4 10.1.250.101 and ipv4 0.0.0.0 0.0.0.0, using call mode noDID and DID. The default mode is no DID, including one-stage dialing. When setting the dealers, you should specify “direct-inward-dial = disabled”.
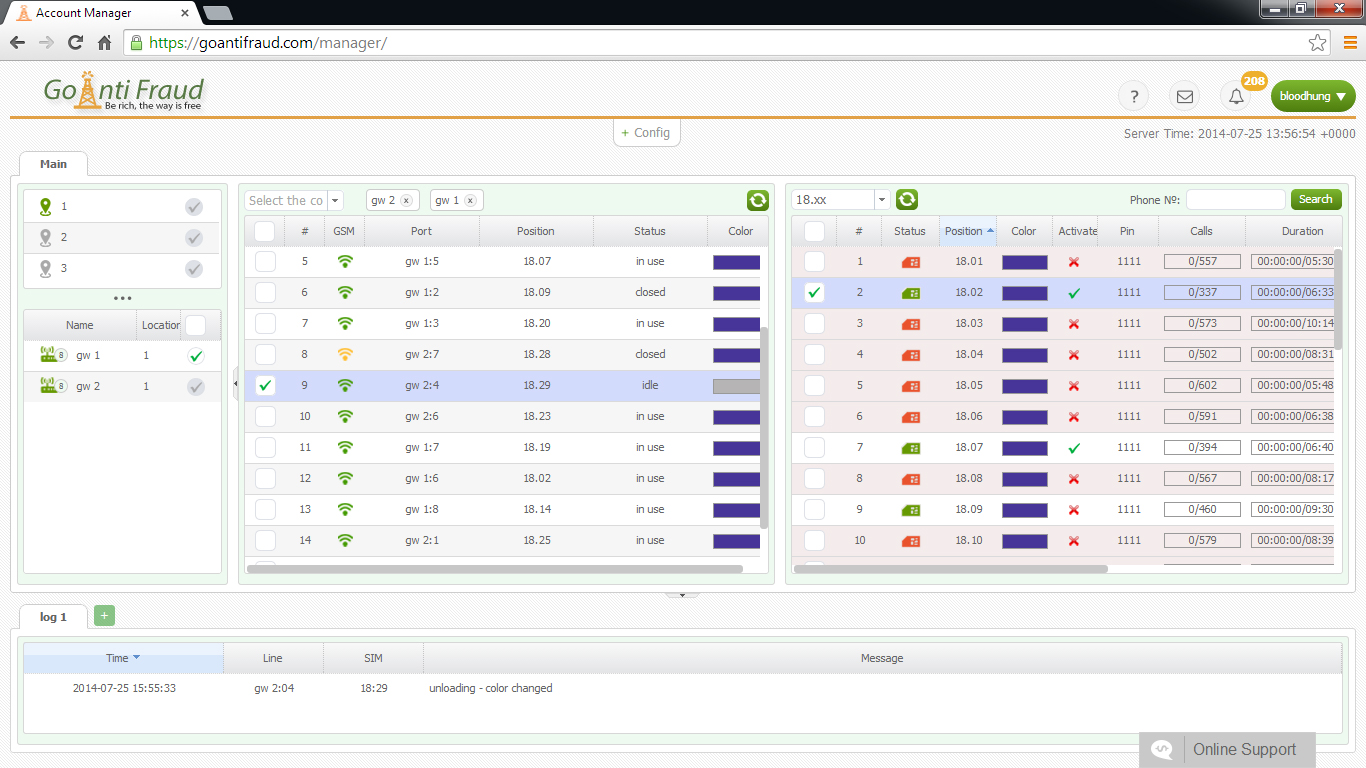
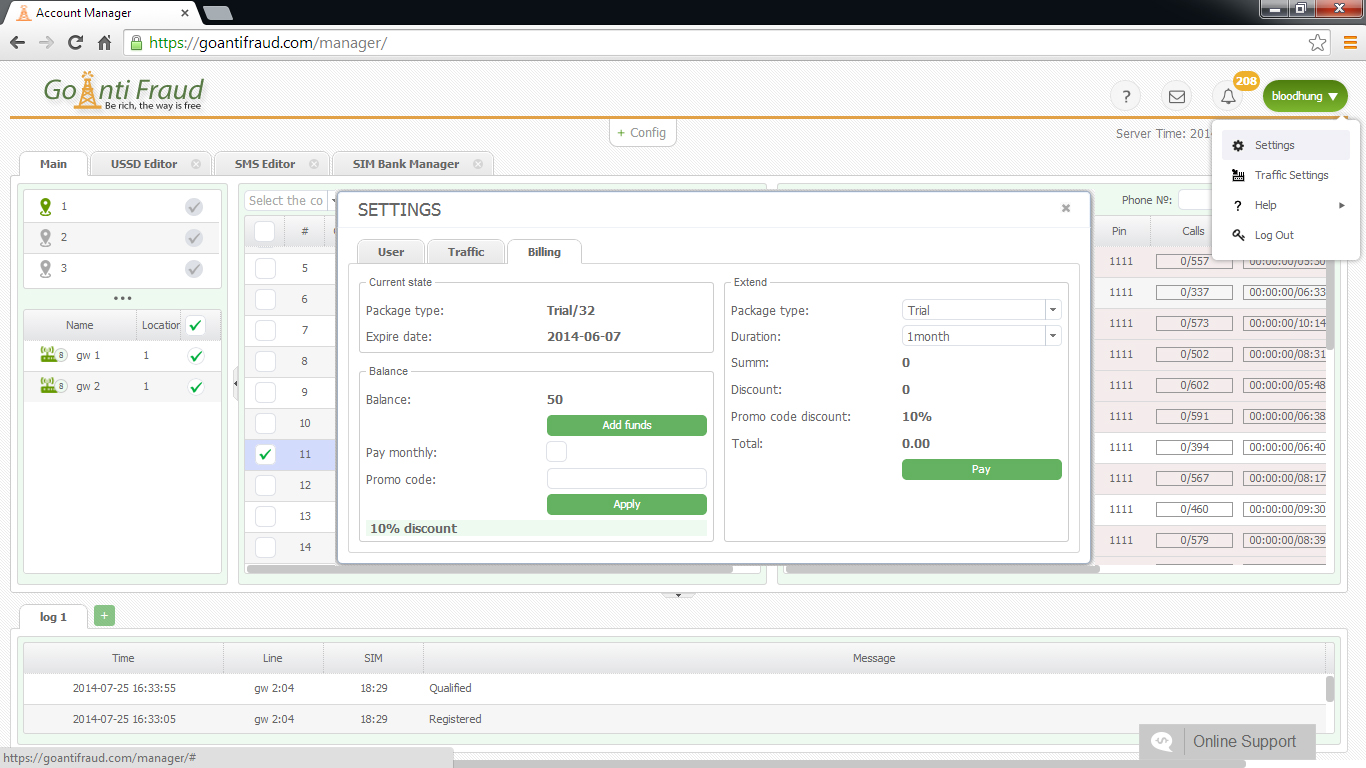
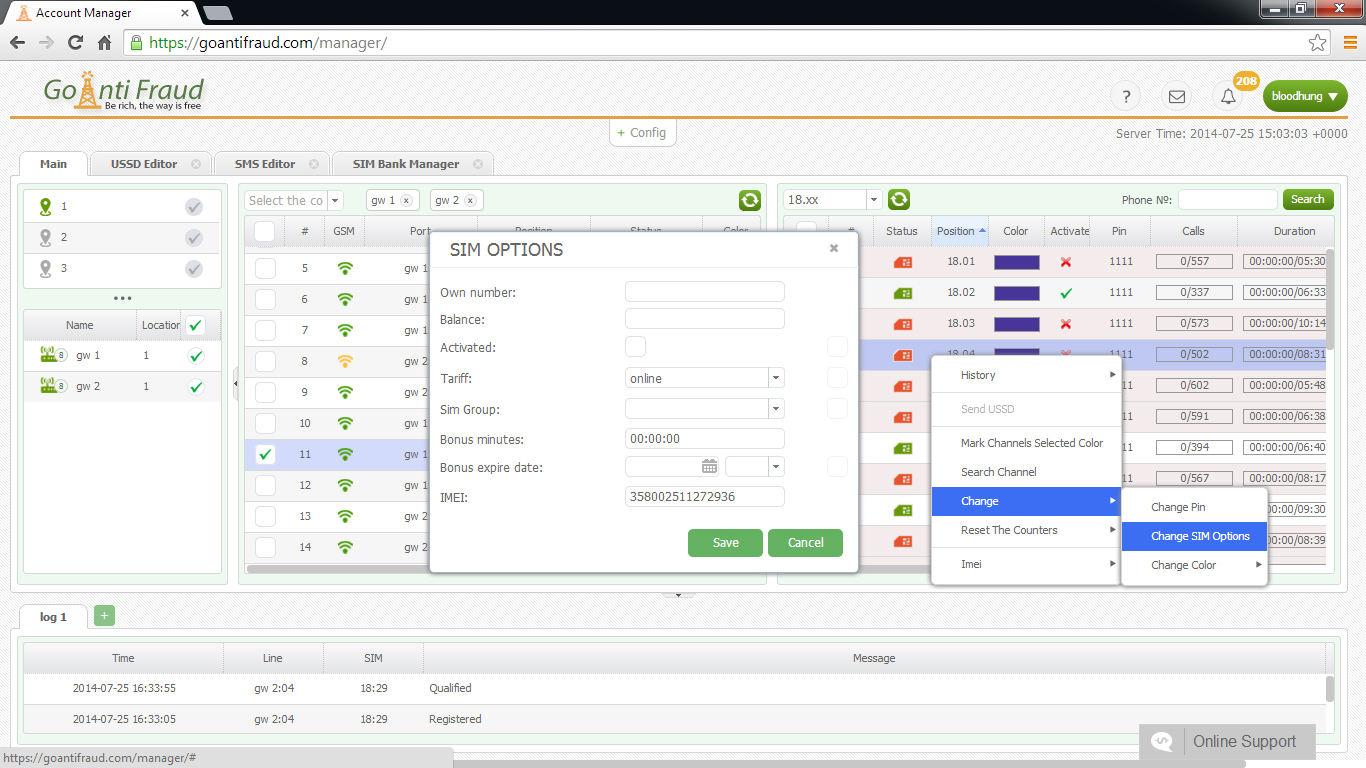
To protect the system, you need to properly configure the Voip-gateway gsm and the intranet firewall. In addition, it is important to monitor the equipment from time to time and make sure that the settings are correct to catch the attackers red-handed.
GoAntiFraud offers you to start a profitable GSM termination business! If you are interested in VoIP technology, we will help you start your own business, yielding a stable income. By purchasing our comprehensive New Business package, you will start making money immediately! We will give you full technical support at all stages of business.