Cellular operators are investing heavily in the development of so-called AntiFraud systems. With their help it is possible to monitor the GSM termination using gateways. When the suspiciously high activity is detected, the systems block SIM-cards, which are used to terminate calls.
AntiFraud analytical and calling systems
Any AntiFraud system includes 2 components - the analytic and calling. The analytic component works by means of the following principle: analyzing the various parameters of the subscriber behavior in a network, it identifies terminated GSM traffic, whereupon the SIM-lock mechanism is activated. The antifraud calling system calls numbers, which fall under the suspicions, by VoIP. If the call takes place, it signals the cellular operator about GSM termination.
"Humanity" Parameters
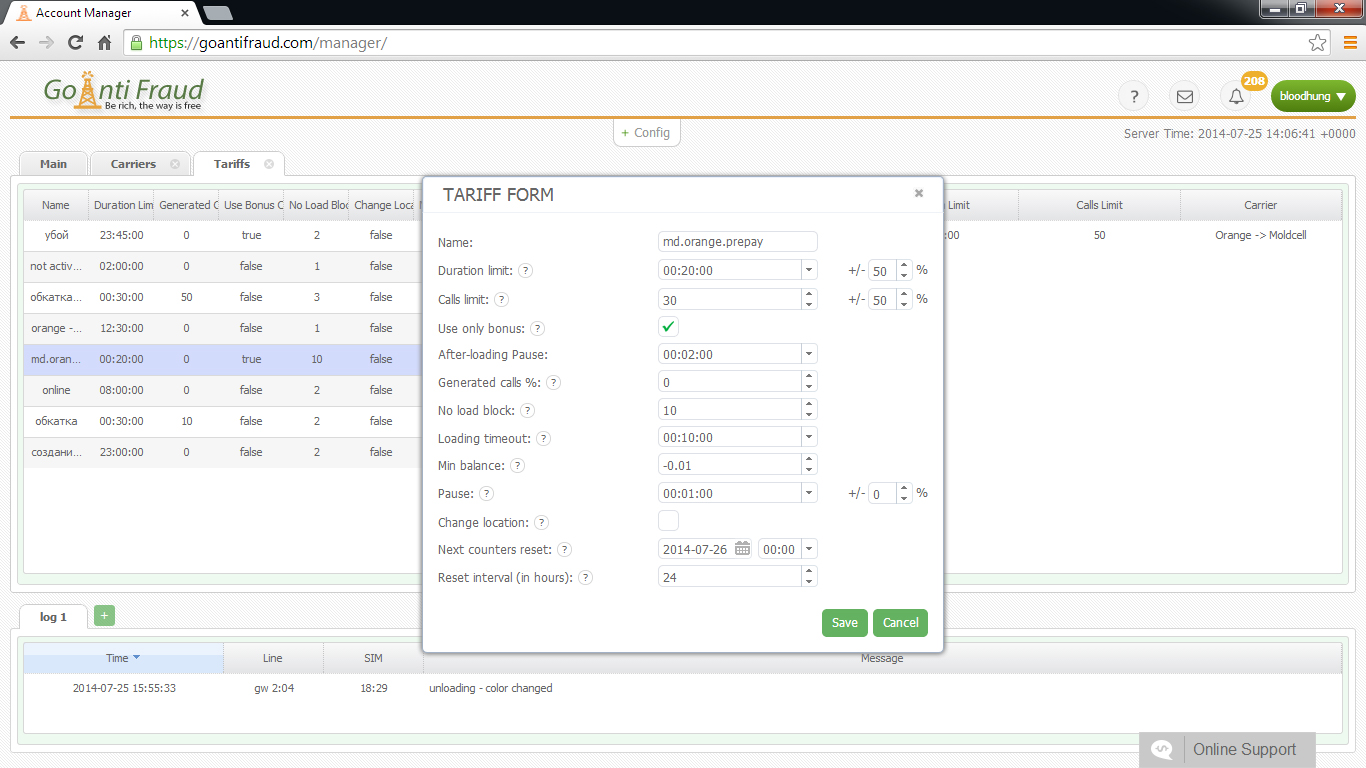
There are special "humanity parameters" to determine terminated SIM-cards. AntiFraud systems allow for certain statistics about the behavior of a real person on the network and compare them with the "behavior" of the SIM-card. It is known that mobile operators are beginning to follow the subscriber number from the activation date.
GoAntiFraud will allow you to minimize the risks of the SIM-lock in the GSM termination. Reduce business costs on the purchase of new SIM-cards by buying the service license and you will get more profit!
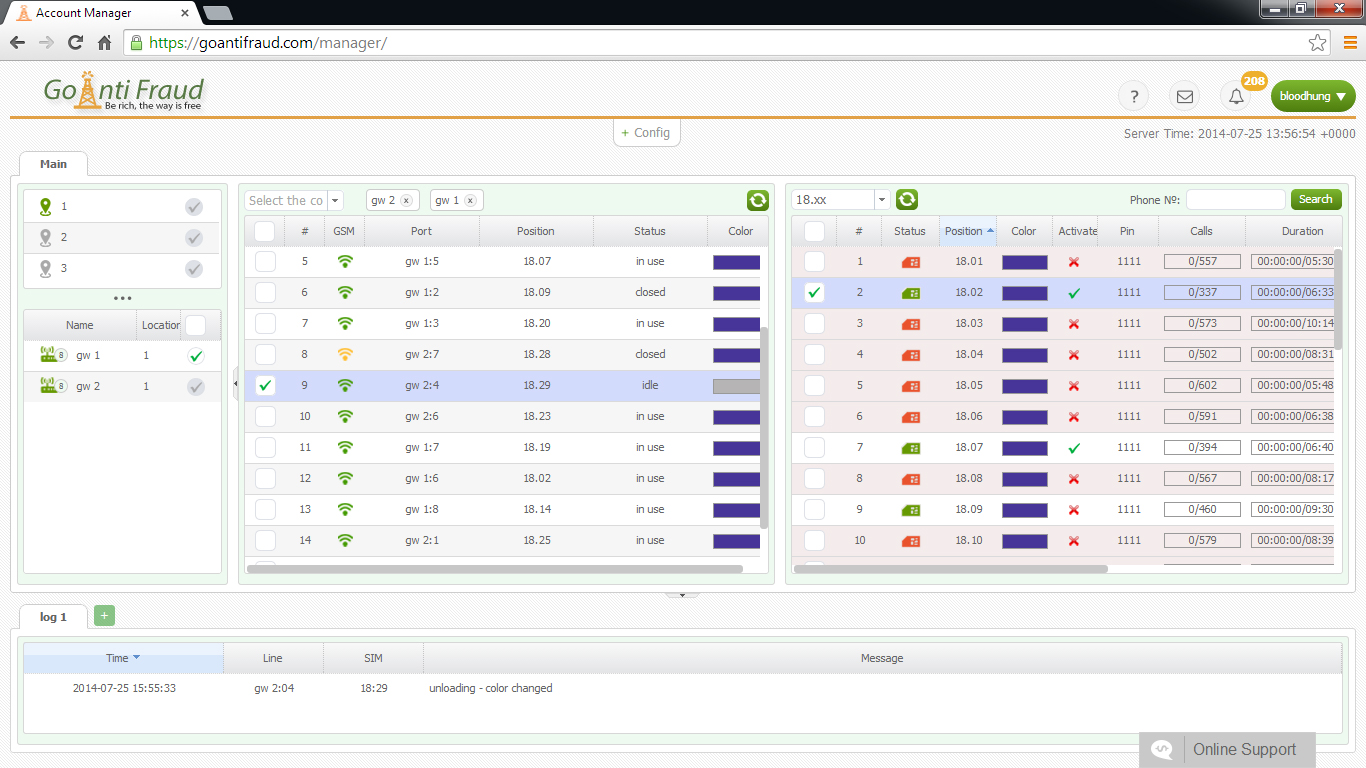
Assessing the SIM-card, the system takes the following parameters into account:
- The number of outgoing calls to different numbers cannot exceed 30 calls by a real person.
- The ratio of outgoing calls and incoming calls should be about 20%.
- The ratio of the total duration of outgoing calls to the total duration of incoming calls.
- "Preferred numbers". These groups of subscriber numbers to which a living person calls frequently, and they call him back. AntiFraud system can also take into account the percentage of calls to "preferred numbers" among the total number of calls.
- The registration of the SIM-card to different base stations, whose coverage does not overlap area for a certain period (typically 1 week).
- The total number of calls to unique numbers for a certain time period.
- The period of activity of SIM-cards during the day (the real user activity changes in the morning, afternoon and night periods).
- The number of calls that are made within the same region (city, region).
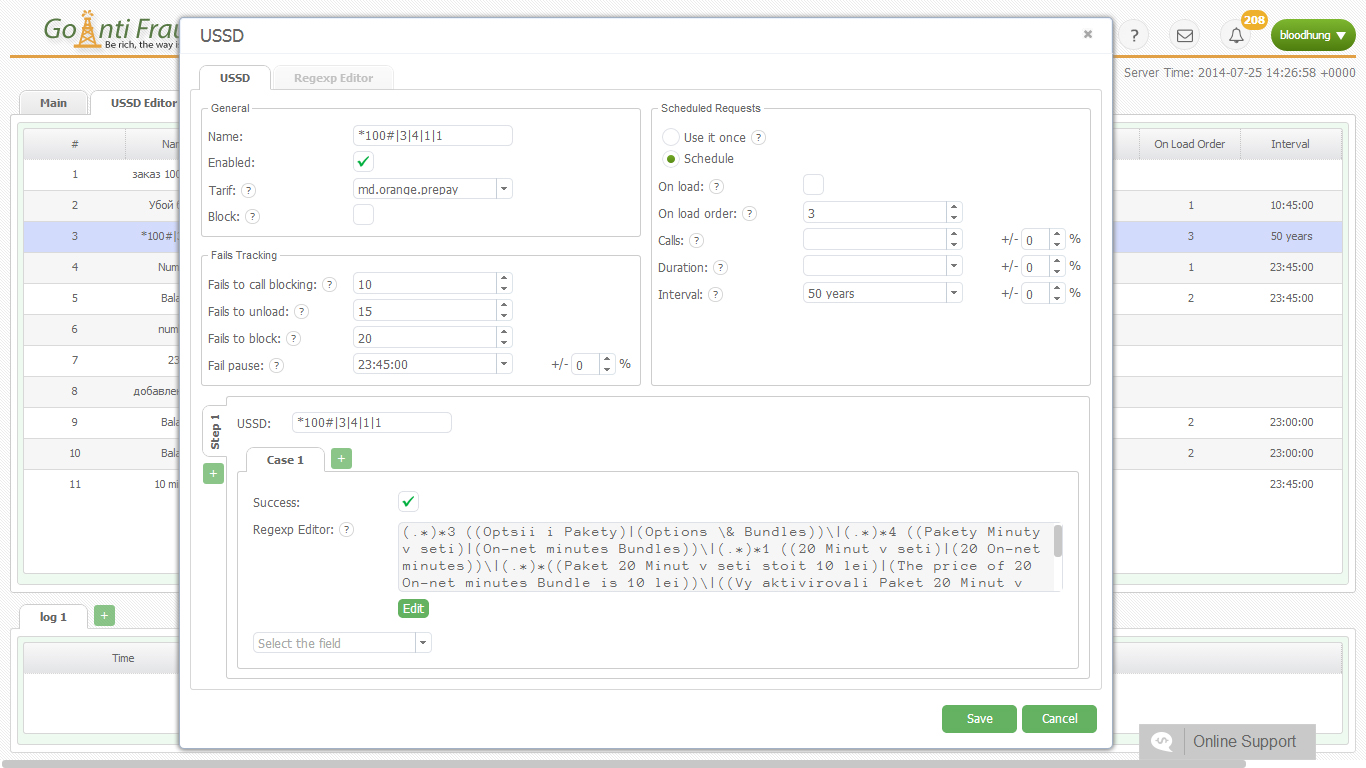
- The number of sent SMS-messages.
- USSD-requests.
- A number of calls to other mobile operators.
- Call Detail Record.
- Changing the type of activity (degree of load on the card) in the business time and "home time".
- SIM card time "on air".
Both the parameters and their numerical values change depending on the mobile operator and country in which the calls are terminated.
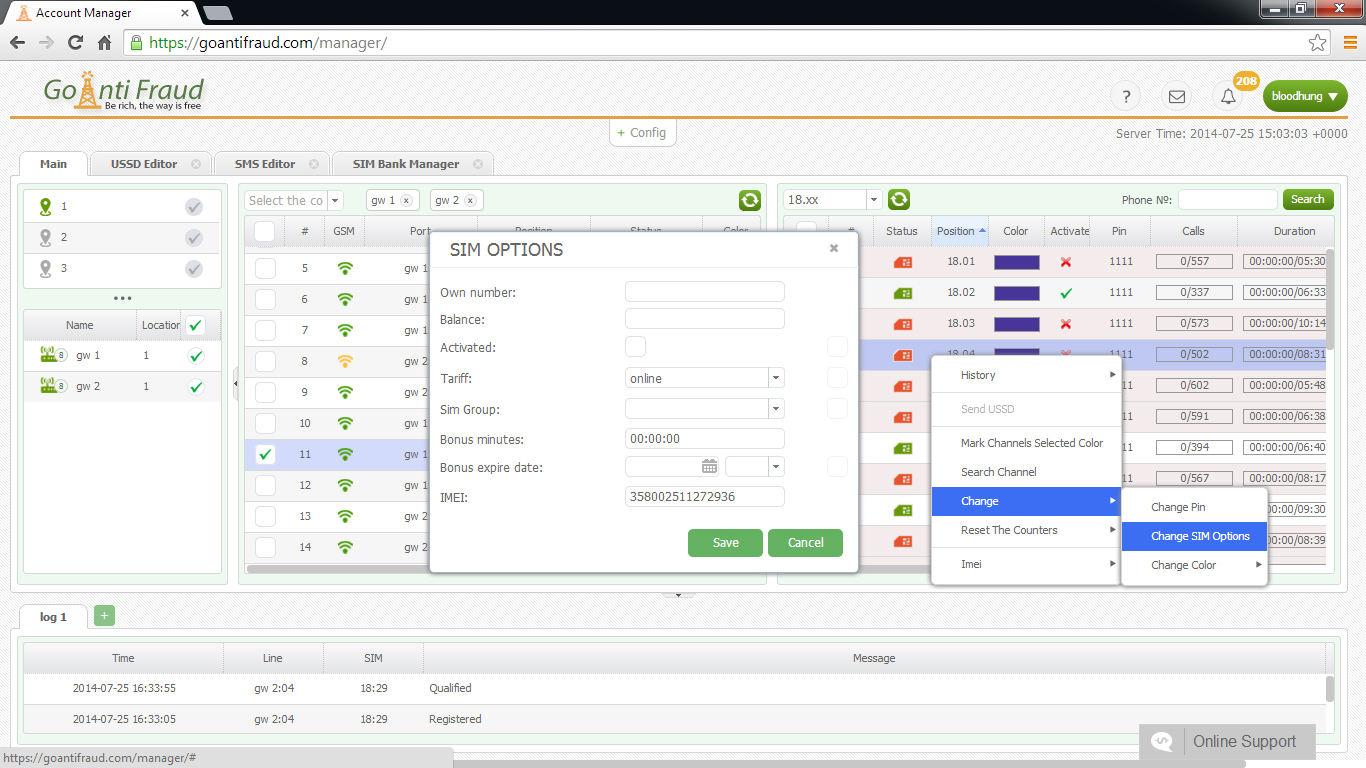
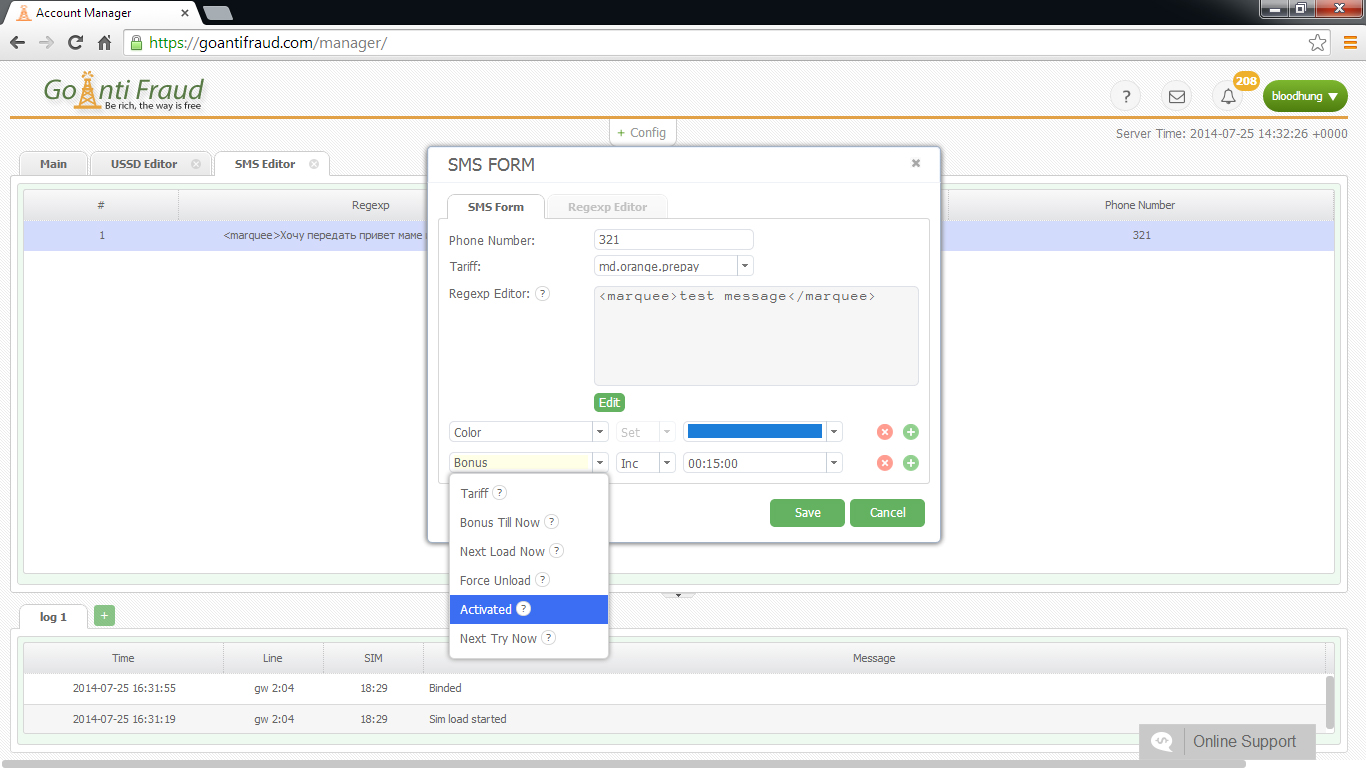
To work around Antifraud systems, terminators use different methods to simulate the behavior of a real user on the network. GoAntiFraud will help you build an efficient GSM termination logic. We offer proven masking tools for SIM-cards and use software for the computerized control of the voip gsm gateway. Our service also helps circumvent the calling by the operator, thanks to the "white" and "black" lists function.